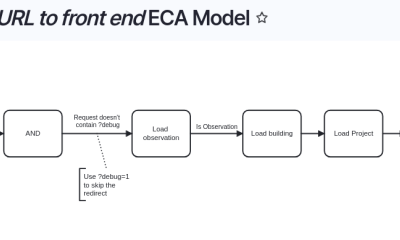
Create a deep redirect in a headless site
One of our clients has a custom surveying application built with a Drupal back end, and a VueJS/headless front end. They use this application to record observations in various buildings and sites that don't meet accessibility requirements.
They give their clients access to the front end. This application organizes observations into particular sites, in particular projects, grouped by the requirement. Each observation can have photos attached, along with notes and recommended solutions.